In software engineering, detecting vulnerabilities in code is a crucial task that ensures the security and reliability of software systems. If left unchecked, vulnerabilities can lead to major security breaches, compromising the integrity of the software and the data it handles. Over the years, the development of automated tools to detect these vulnerabilities has become increasingly important, particularly as software systems become more complex and interconnected.
A major challenge in developing these automated tools is the lack of large and diverse datasets required to effectively train deep learning-based vulnerability detection (DLVD) models. Without sufficient data, these models struggle to accurately identify and generalize across different types of vulnerabilities. This problem is compounded by the fact that existing methods for generating vulnerable code samples are typically limited in scope, focus on specific types of vulnerabilities, and require large, well-curated datasets to be effective.
Traditionally, methods for generating vulnerable code have relied on methods such as mutation and injection. Mutation involves altering vulnerable code samples to create new ones, maintaining the functionality of the code while introducing slight variations. In contrast, injection involves inserting vulnerable code segments into clean code to generate new samples. While these methods have shown promise, they often have limitations in generating diverse and complex vulnerabilities, which are crucial for training robust DLVD models.
Researchers from the University of Manitoba and Washington State University introduced a new approach called VulScribeR, designed to address these challenges. VulScribeR employs large language models (LLMs) to generate diverse and realistic vulnerable code samples through three strategies: mutation, injection, and extension. This approach leverages advanced techniques such as recovery-augmented generation (RAG) and clustering to improve the diversity and relevance of the generated samples, making them more effective for training DLVD models.
The methodology behind VulScribeR is sophisticated and well-structured. The mutation strategy asks the LLM to modify vulnerable code samples, ensuring that the changes do not alter the original functionality of the code. The injection strategy involves retrieving similar vulnerable and clean code samples, and the LLM injects the vulnerable logic into the clean code to create new samples. The extension strategy takes this a step further by incorporating parts of clean code into already vulnerable samples, thus improving the contextual diversity of the vulnerabilities. To ensure the quality of the generated code, a fuzzy analyzer filters out invalid or syntactically incorrect samples.
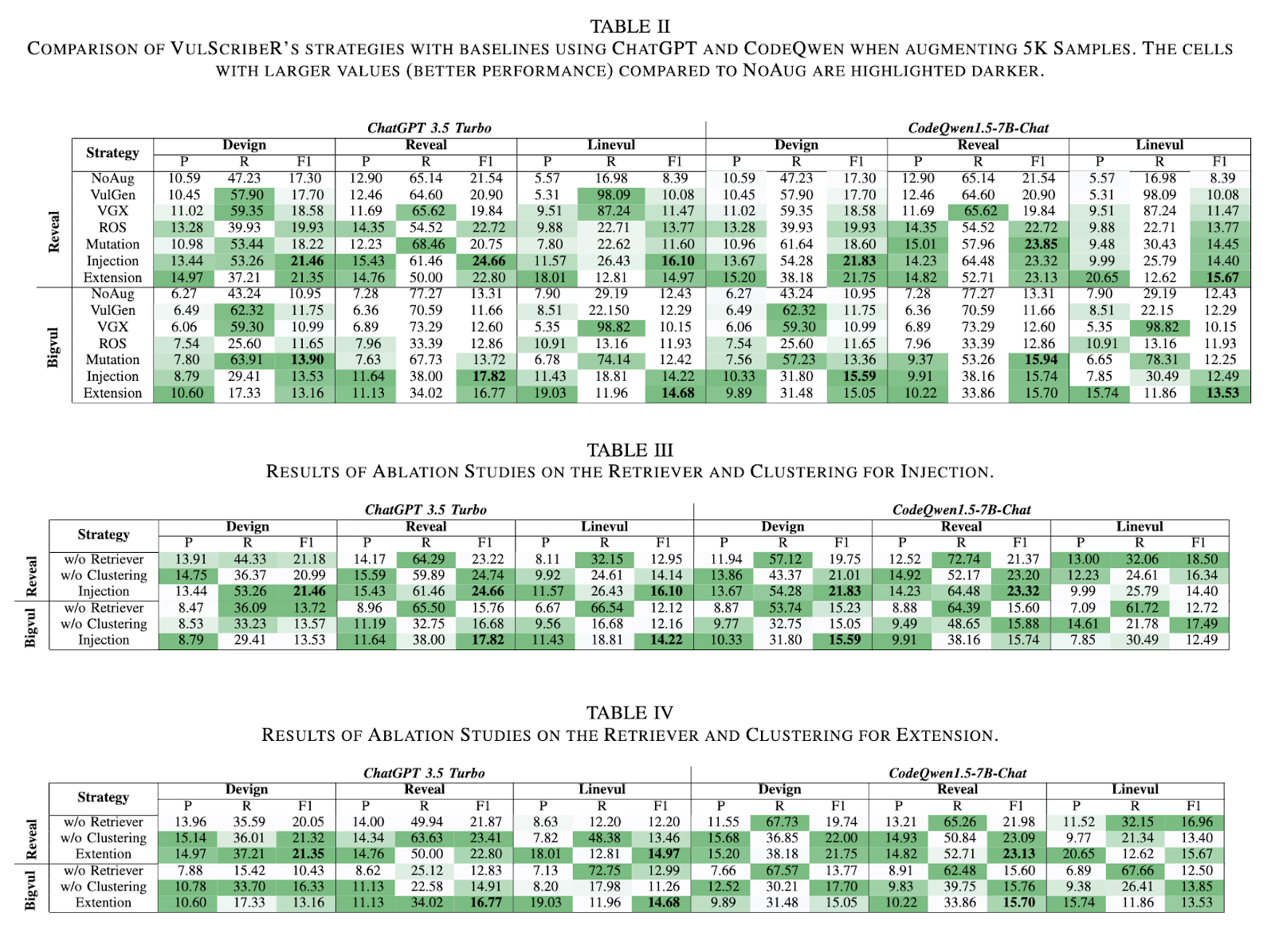
In terms of performance, VulScribeR has demonstrated significant improvements over existing methods. The injection strategy, for example, outperformed several baseline approaches including NoAug, VulGen, VGX, and ROS, with F1-score improvements of 30.80%, 27.48%, 27.93%, and 15.41%, respectively, when generating an average of 5,000 vulnerable samples. When scaled up to 15,000 samples, the injection strategy achieved even more impressive results, outperforming the same baselines by 53.84%, 54.10%, 69.90%, and 40.93%. These results underscore the effectiveness of VulScribeR in generating high-quality, diverse datasets that significantly improve the performance of DLVD models.
The success of VulScribeR highlights the importance of large-scale data augmentation in the field of vulnerability detection. By generating diverse and realistic vulnerable code samples, this approach provides a practical solution to the data sparsity problem that has long hampered the development of effective DLVD models. VulScribeR’s innovative use of LLM, combined with advanced data augmentation techniques, represents a significant advancement in the field, paving the way for more effective and scalable vulnerability detection tools in the future.
Take a look at the PaperAll credit for this research goes to the researchers of this project. Also, don't forget to follow us on twitter.com/Marktechpost”>twitter and join our Telegram Channel and LinkedIn GrAbove!. If you like our work, you will love our fact sheet..
Don't forget to join our Subreddit with over 48 billion users
Find upcoming ai webinars here
Nikhil is a Consultant Intern at Marktechpost. He is pursuing an integrated dual degree in Materials from Indian Institute of technology, Kharagpur. Nikhil is an ai and Machine Learning enthusiast who is always researching applications in fields like Biomaterials and Biomedical Science. With a strong background in Materials Science, he is exploring new advancements and creating opportunities to contribute.
<script async src="//platform.twitter.com/widgets.js” charset=”utf-8″>