Amazon Bedrock is a fully managed service provided by AWS that gives developers access to base models (FM) and the tools to customize them for specific applications. It allows developers to build and scale generative ai applications using FM through an API, without managing infrastructure. You can choose from several Amazon FMs and leading ai startups, such as AI21 Labs, Anthropic, Cohere, and Stability ai, to find the model that best suits your use case. With Amazon Bedrock’s serverless experience, you can get started quickly, easily experiment with FM, customize it privately with your own data, and seamlessly integrate and deploy it into your applications using AWS tools and capabilities.
Customers are building innovative generative ai applications using Amazon Bedrock APIs using their own proprietary data. When accessing Amazon Bedrock APIs, customers are looking for a mechanism to set up a data perimeter without exposing their data to the Internet in order to mitigate potential threat vectors from Internet exposure. The Amazon Bedrock VPC Endpoint powered by AWS PrivateLink allows you to establish a private connection between your account’s VPC and the Amazon Bedrock service account. Allows VPC instances to communicate with service resources without requiring public IP addresses.
In this post, we demonstrate how to configure private access in your AWS account to access Amazon Bedrock APIs through PrivateLink-powered VPC endpoints to help you securely build generative ai applications with your own data.
Solution Overview
You can use generative ai to develop a wide range of applications, such as text summarization, content moderation, and other capabilities. When building these types of generative ai applications using FM or base models, customers want to generate a response without resorting to the public Internet or based on their proprietary data that may reside in their company’s databases.
In the following diagram, we represent an architecture for configuring your infrastructure to read your proprietary data residing in Amazon Relational Database Service (Amazon RDS) and augment the Amazon Bedrock API request with product information when answering product-related queries from your generative ai application. . Although we use Amazon RDS in this diagram for illustrative purposes, you can test end-to-end private access to Amazon Bedrock APIs by following the instructions provided in this post.
The workflow steps are as follows:
- AWS Lambda running in your private VPC subnet receives the fast request from the generative ai application.
- Lambda makes a call to the proprietary RDS database and augments the quick query context (for example, adding product information) and invokes the Amazon Bedrock API with the augmented query request.
- The API call is routed to the Amazon Bedrock VPC endpoint that is associated with the VPC endpoint policy with Allow permissions for Amazon Bedrock APIs.
- The Amazon Bedrock service API endpoint receives the API request over PrivateLink without traversing the public Internet.
- You can change the Amazon Bedrock VPC endpoint policy to Deny Permissions to validate that calls to Amazon Bedrock APIs are denied.
- You can also privately access Amazon Bedrock APIs through the VPC endpoint from your corporate network through an AWS Direct Connect gateway.
Previous requirements
Before you begin, make sure you have the following prerequisites:
- An AWS account
- An AWS Identity and Access Management (IAM) federation role with access to do the following:
- Create, edit, view, and delete VPC network resources
- Create, edit, view and delete Lambda functions
- Create, edit, view, and delete IAM roles and policies
- List foundation models and invoke the Amazon Bedrock foundation model
- For this publication we use the
us-east-1Region - Request access to the base model through the Amazon Bedrock console
Configure private access infrastructure.
In this section, we configure the infrastructure such as VPC, private subnets, security groups, and Lambda function using an AWS CloudFormation template.
Use the following template to create the infrastructure stack Bedrock-GenAI-Stack in your AWS account.
The CloudFormation template creates the following resources on your behalf:
- A VPC with two private subnets in separate availability zones
- Security groups and routing tables
- IAM role and policies for using Lambda, Amazon Bedrock, and Amazon Elastic Compute Cloud (Amazon EC2)
Configure the VPC endpoint for Amazon Bedrock
In this section, we use Amazon Virtual Private Cloud (Amazon VPC) to configure the VPC endpoint for Amazon Bedrock to facilitate private connectivity from your VPC to Amazon Bedrock.
- In the Amazon VPC console, under virtual private cloud In the navigation pane, choose End points.
- Choose Create endpoint.
- For name tagget into
bedrock-vpce. - Low Servicessearch for bedrock-runtime and select
com.amazonaws.<region>.bedrock-runtime. - For VPCspecify the VPC
Bedrock-GenAI-Project-vpcwhich you created via the CloudFormation stack in the previous section.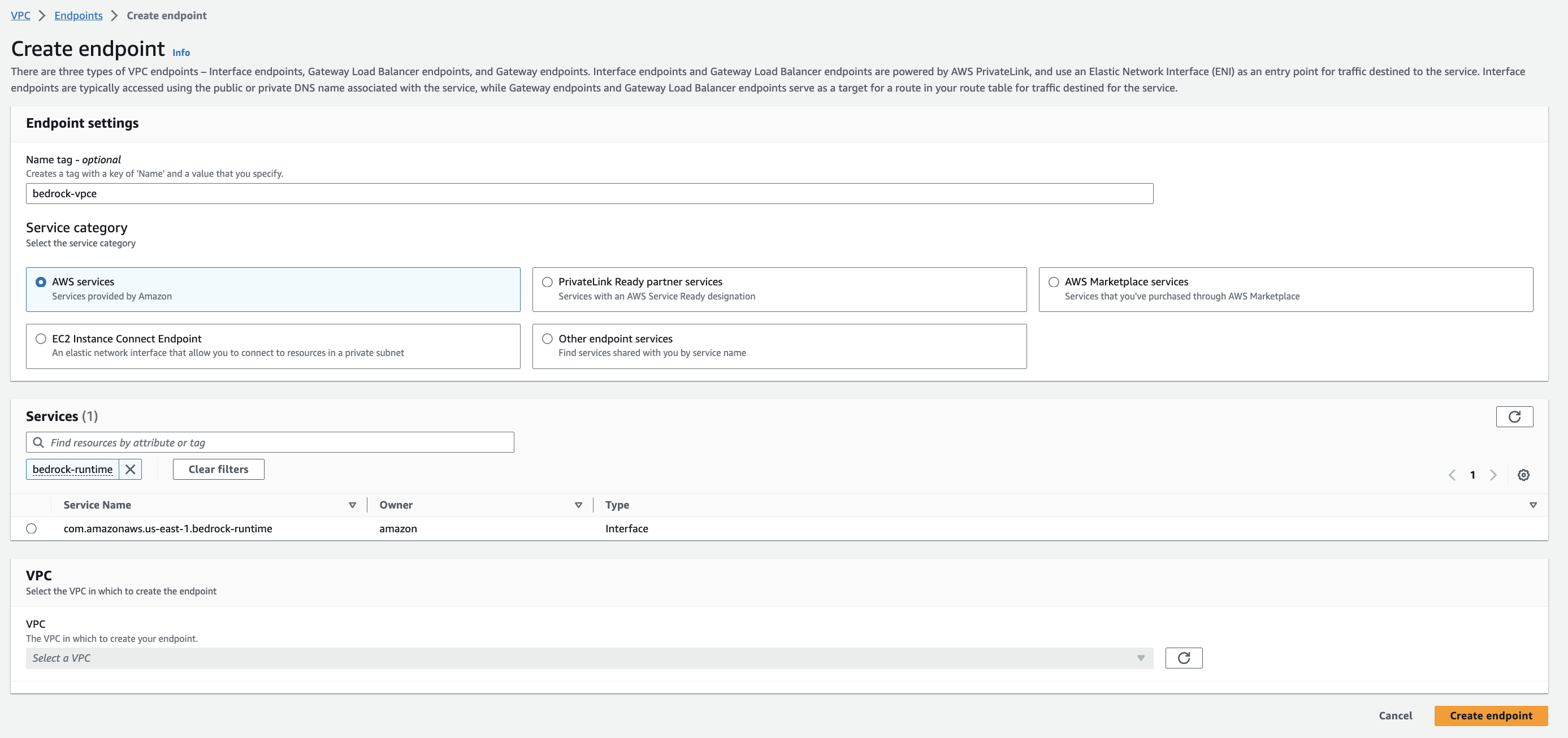
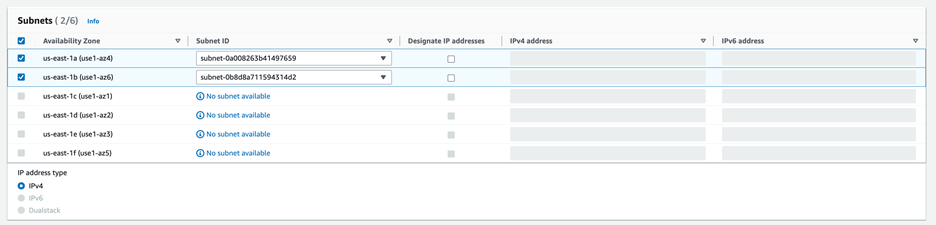
- In it Subnets and select the availability zones and choose the corresponding subnet IDs from the drop-down menu.
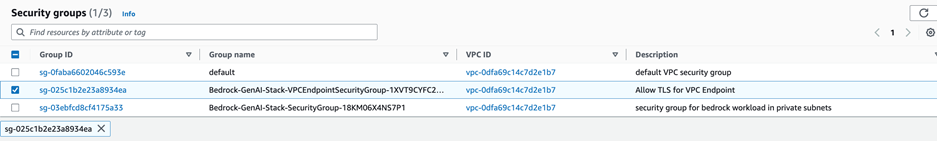
- For security groupsselect security group with group name
Bedrock-GenAI-Stack-VPCEndpointSecurityGroup-and descriptionAllow TLS for VPC Endpoint.
A security group acts as a virtual firewall for your instance to control incoming and outgoing traffic. Note that this VPC endpoint security group only allows traffic originating from the attached security group to its private VPC subnets, adding a layer of protection.
- Choose Create endpoint.
- In it Policy section, select Habit and enter the following least privilege policy to ensure that only certain actions are allowed on the specified base model resource,
arn:aws:bedrock:*::foundation-model/anthropic.claude-instant-v1for a given principal (such as the Lambda function’s IAM role).
It may take up to 2 minutes for the interface endpoint to be created and the status to change to Available. You can refresh the page to check the latest status.
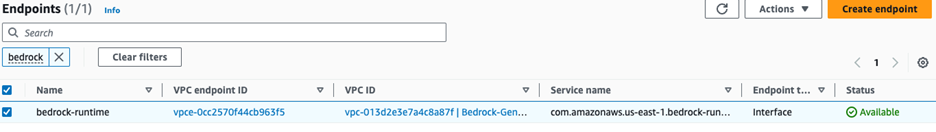
Configure Lambda function on private VPC subnets
Complete the following steps to configure the Lambda function:
- In the Lambda console, choose Features in the navigation panel.
- Choose the function
gen-ai-lambda-stack-BedrockTestLambdaFunction-XXXXXXXXXXXX.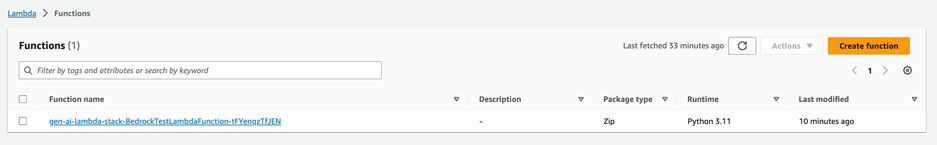
- About him Setting tab, choose Permissions in the left panel.
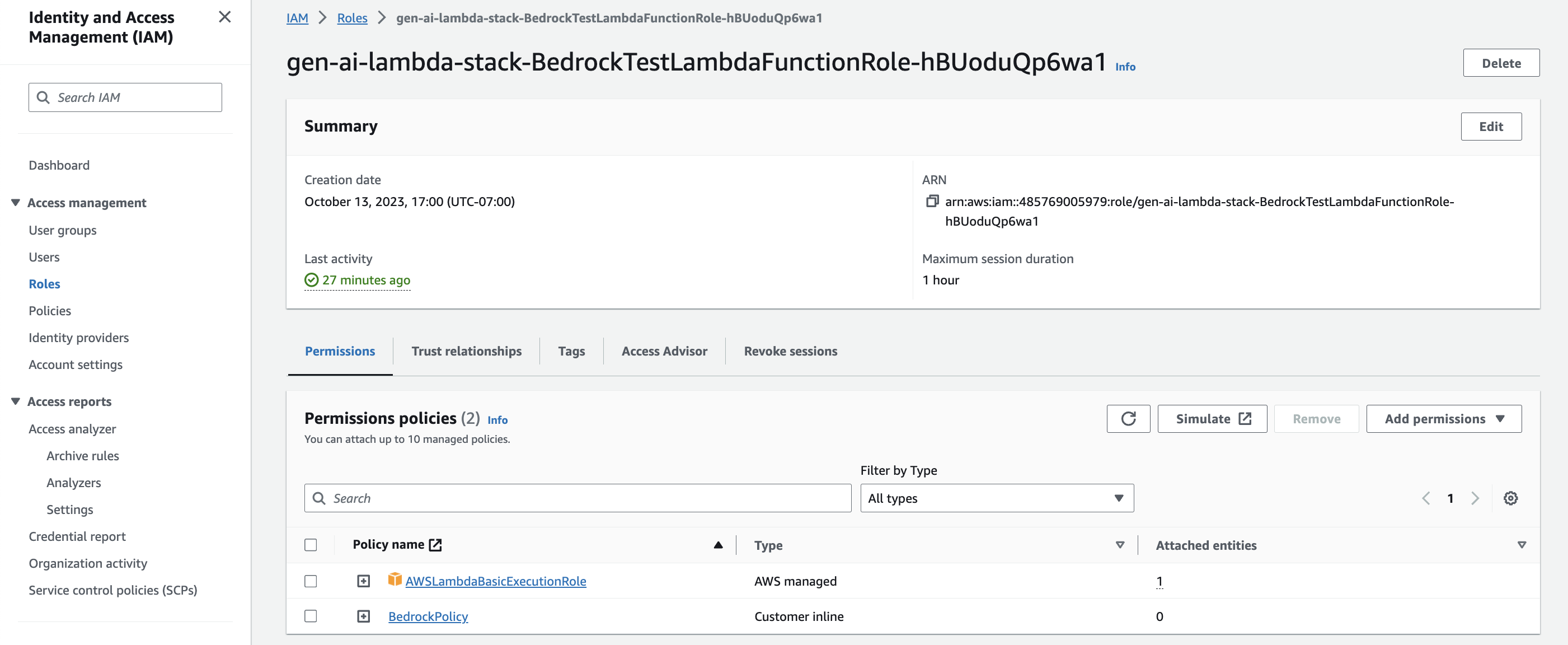
- Low Execution role¸ choose the link for the role
gen-ai-lambda-stack-BedrockTestLambdaFunctionRole-XXXXXXXXXXXX.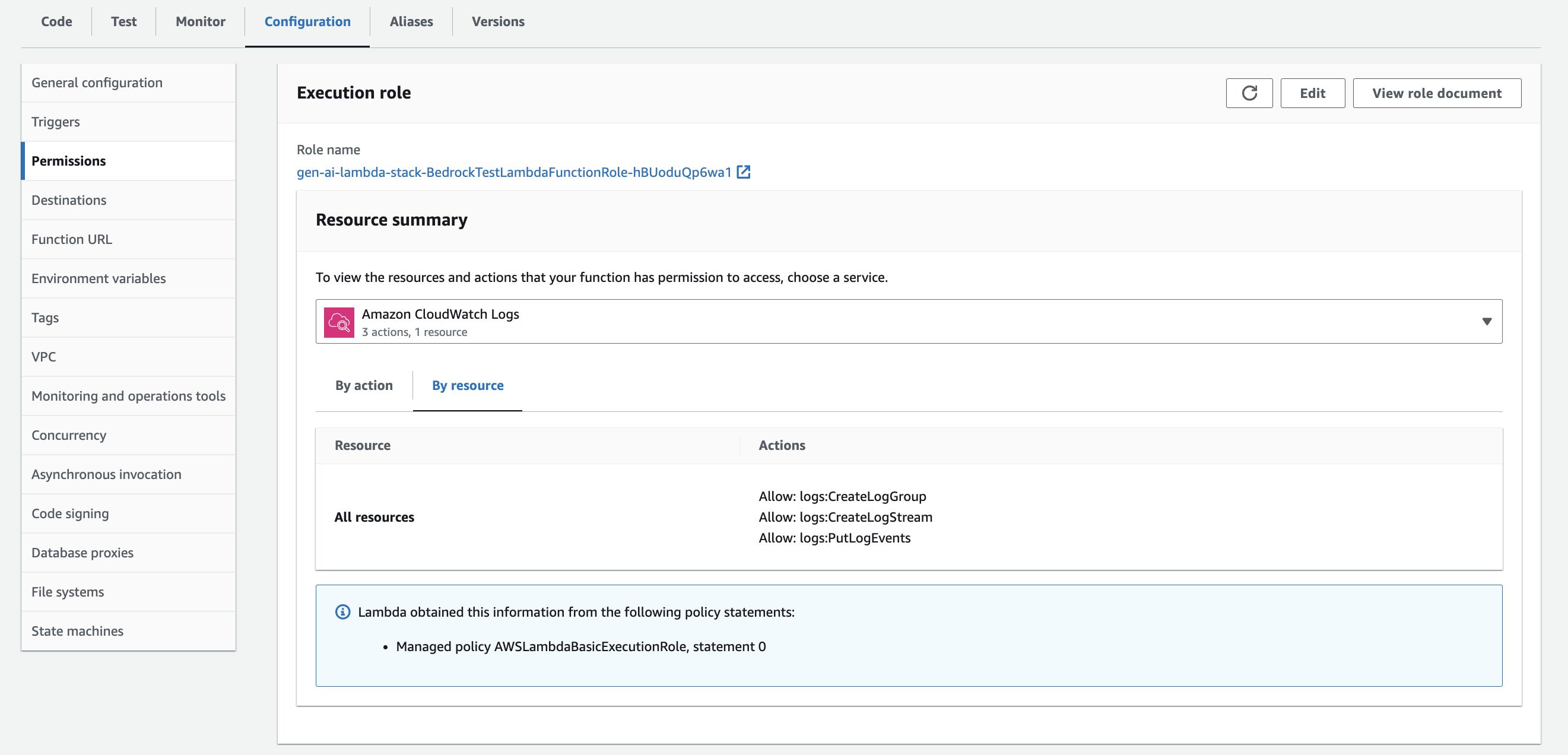
You will be redirected to the IAM console.
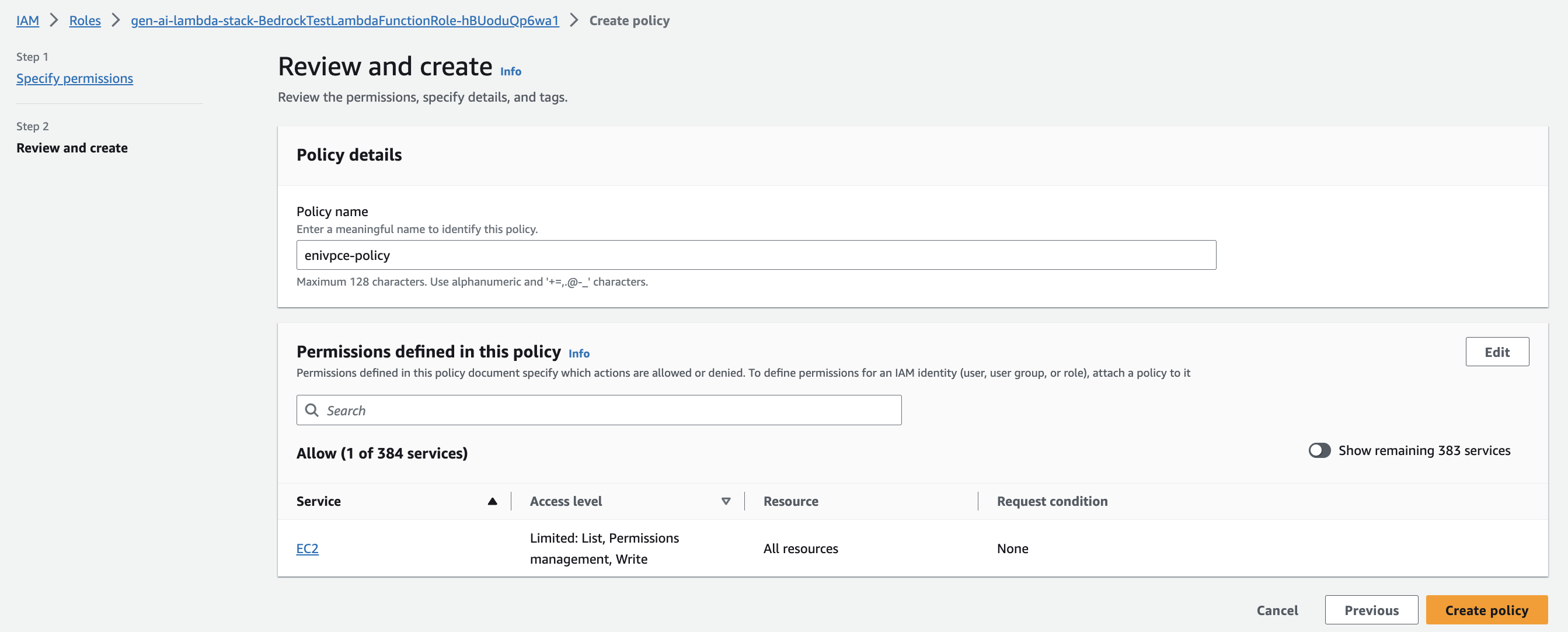
- In it Permission policies section, choose Add permissions and choose Create online policy.
- About him JSON modify the policy as follows:
- Choose Next.
- For Policy nameget into
enivpce-policy. - Choose Create policy.
- Add the following inline policy (provide your source VPC endpoints) to restrict Lambda access to Amazon Bedrock APIs only through VPC endpoints:
- On the Lambda function page, in the Setting tab, choose VPC in the left panel, then choose Edit.
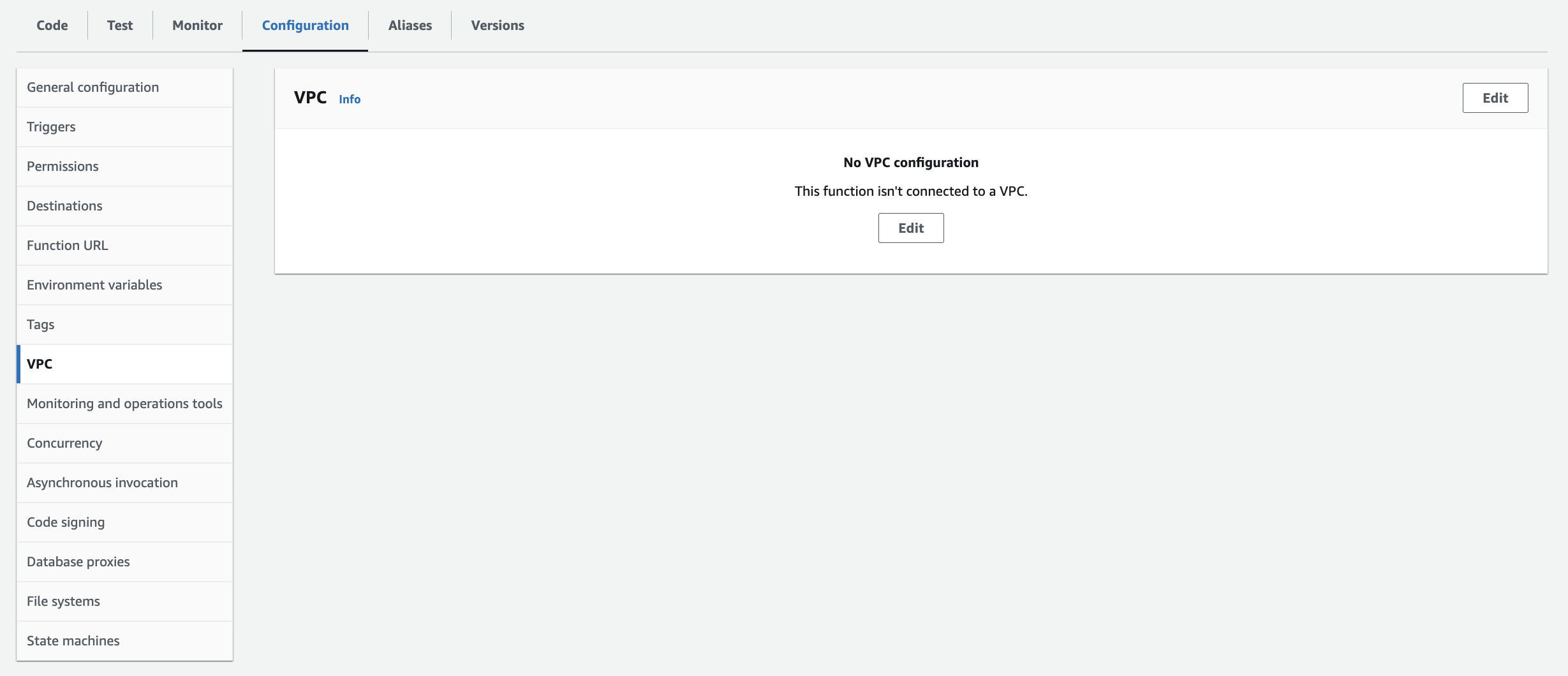
- For VPCchoose
Bedrock-GenAI-Project-vpc. - For Subnetschoose private subnets.
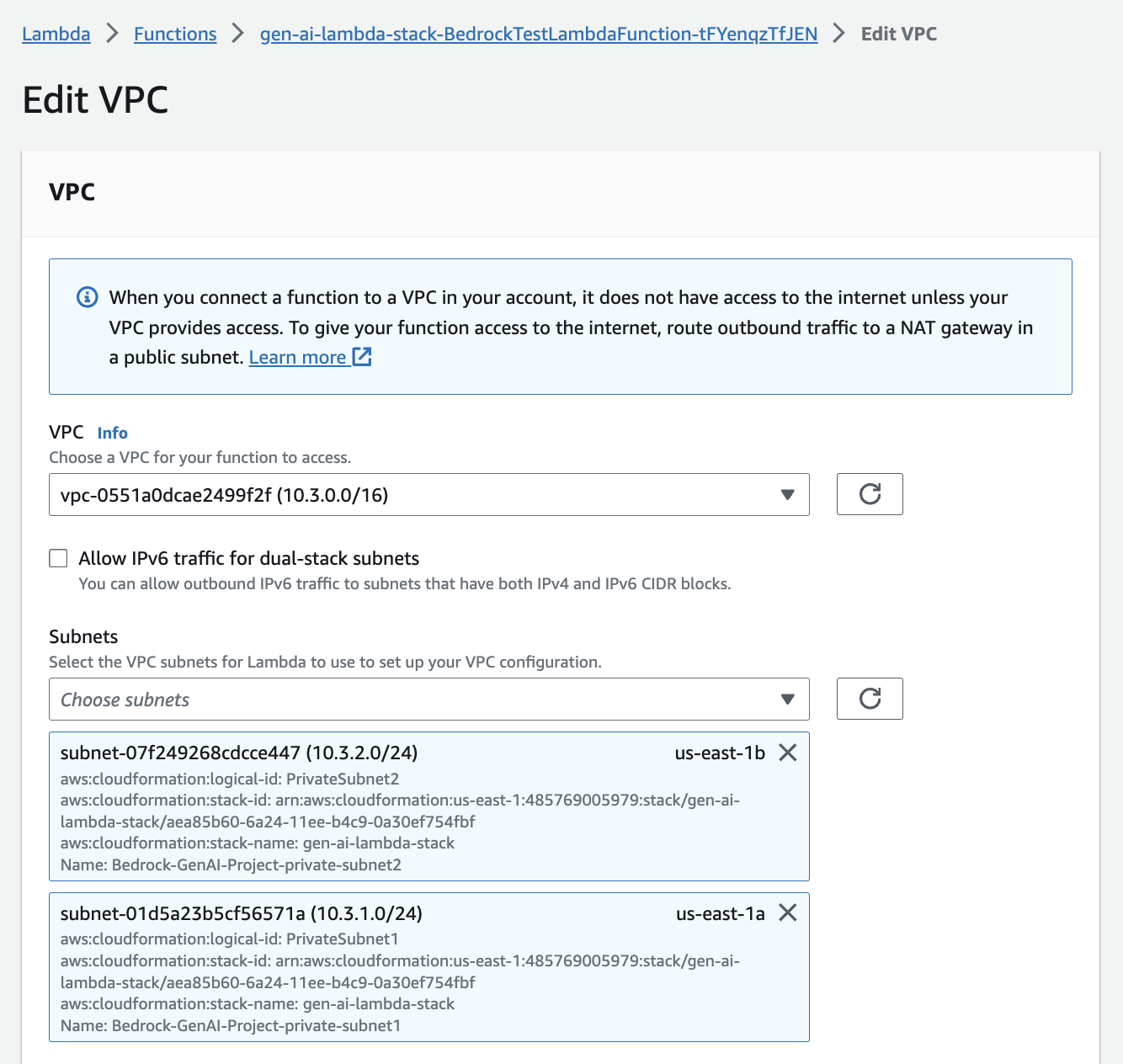
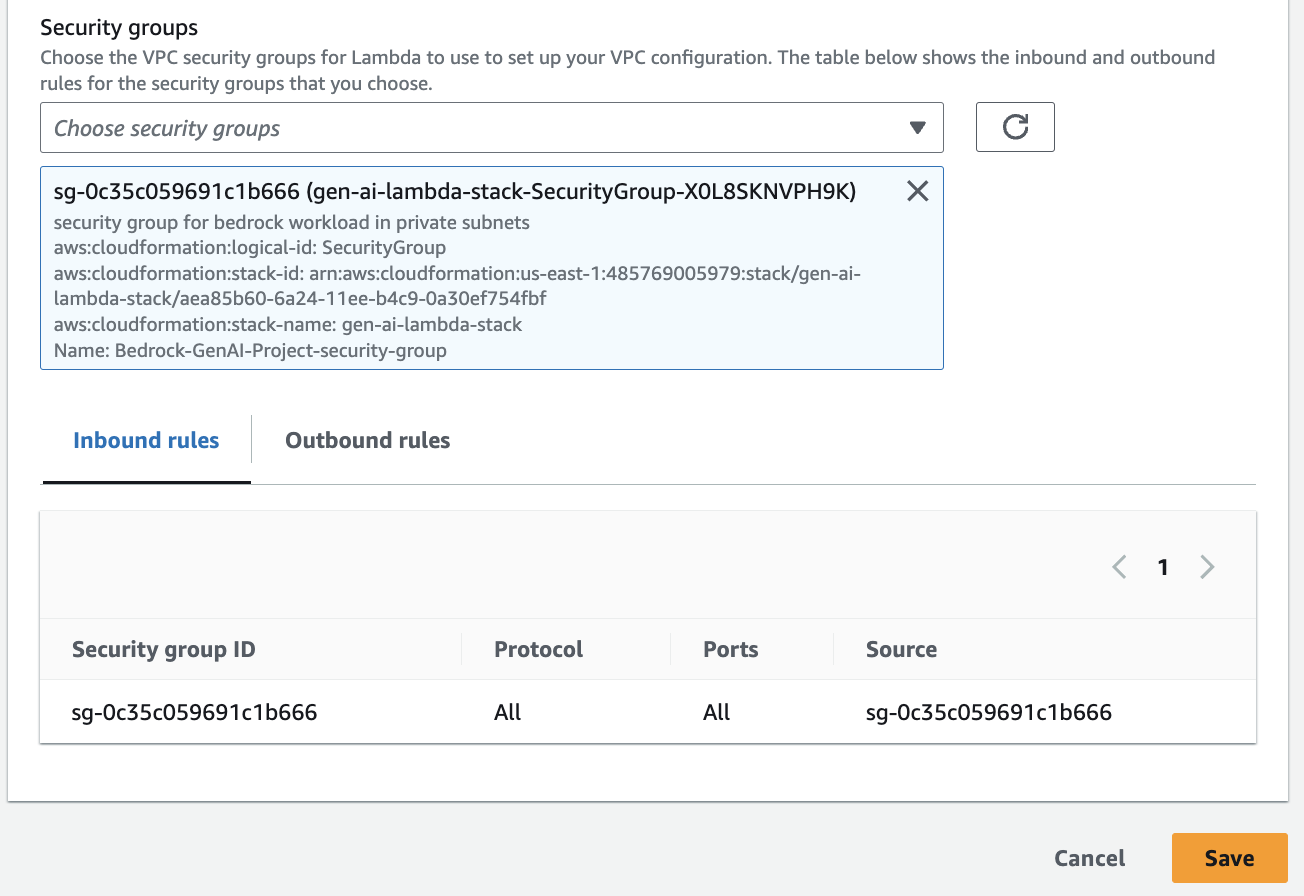
- For security groupschoose
gen-ai-lambda-stack-SecurityGroup-(the security group for the Amazon Bedrock workload on private subnets). - Choose Save.
Test private access controls
You can now test private access controls (Amazon Bedrock API over VPC endpoints).
- In the Lambda console, choose Features in the navigation panel.
- Choose the function
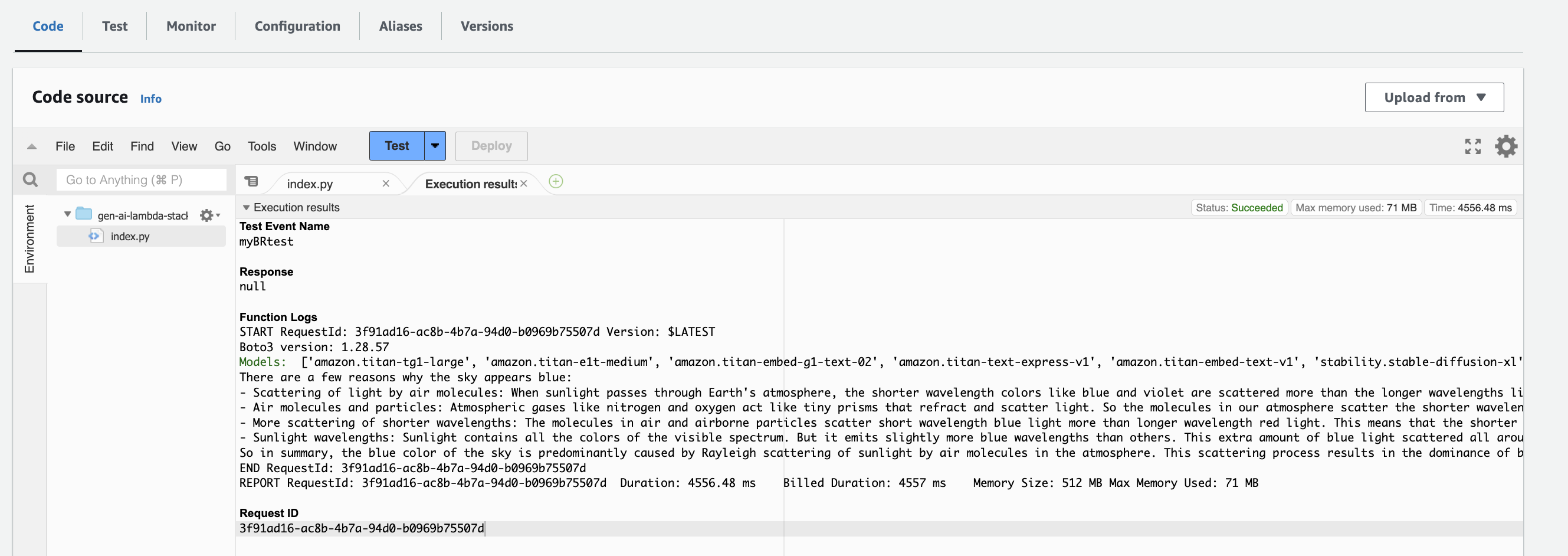
gen-ai-lambda-stack-BedrockTestLambdaFunction-XXXXXXXXXXXX. - About him Code tab, choose Proof.
You should see the following response from the Amazon Bedrock API call (Status: Success).
- To deny access to Amazon Bedrock APIs through VPC endpoints, navigate to the Amazon VPC console.
- Low virtual private cloud In the navigation pane, choose End points.
- Choose your policy and navigate to the Policy tab.
Currently, the VPC endpoint policy is set to Allow.
- To deny access, choose Edit policy.
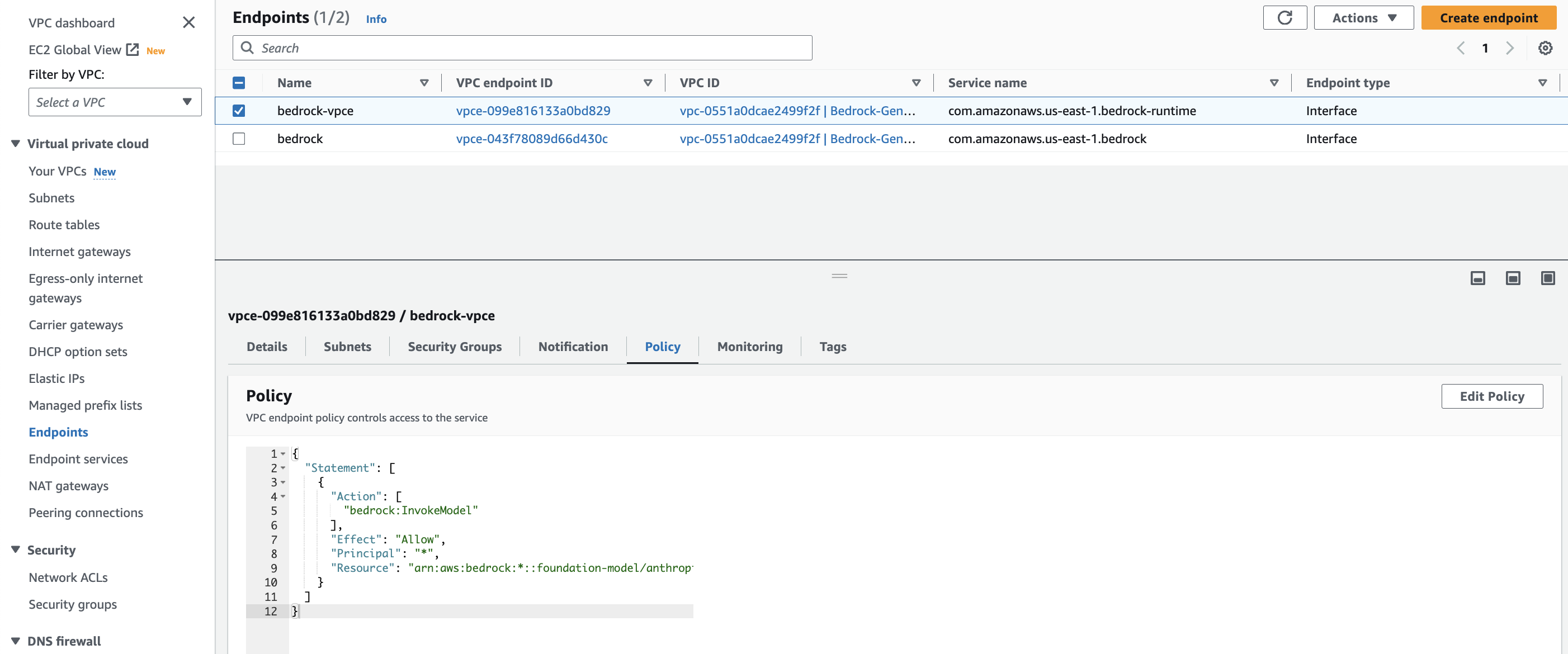
- Change
AllowtoDenyand choose Save.
The VPC endpoint policy can take up to 2 minutes to update.
- Return to the Lambda functions page and in the Code tab, choose Proof.
As shown in the following screenshot, the request to access Amazon Bedrock through the VPC endpoint was denied (status: failed).
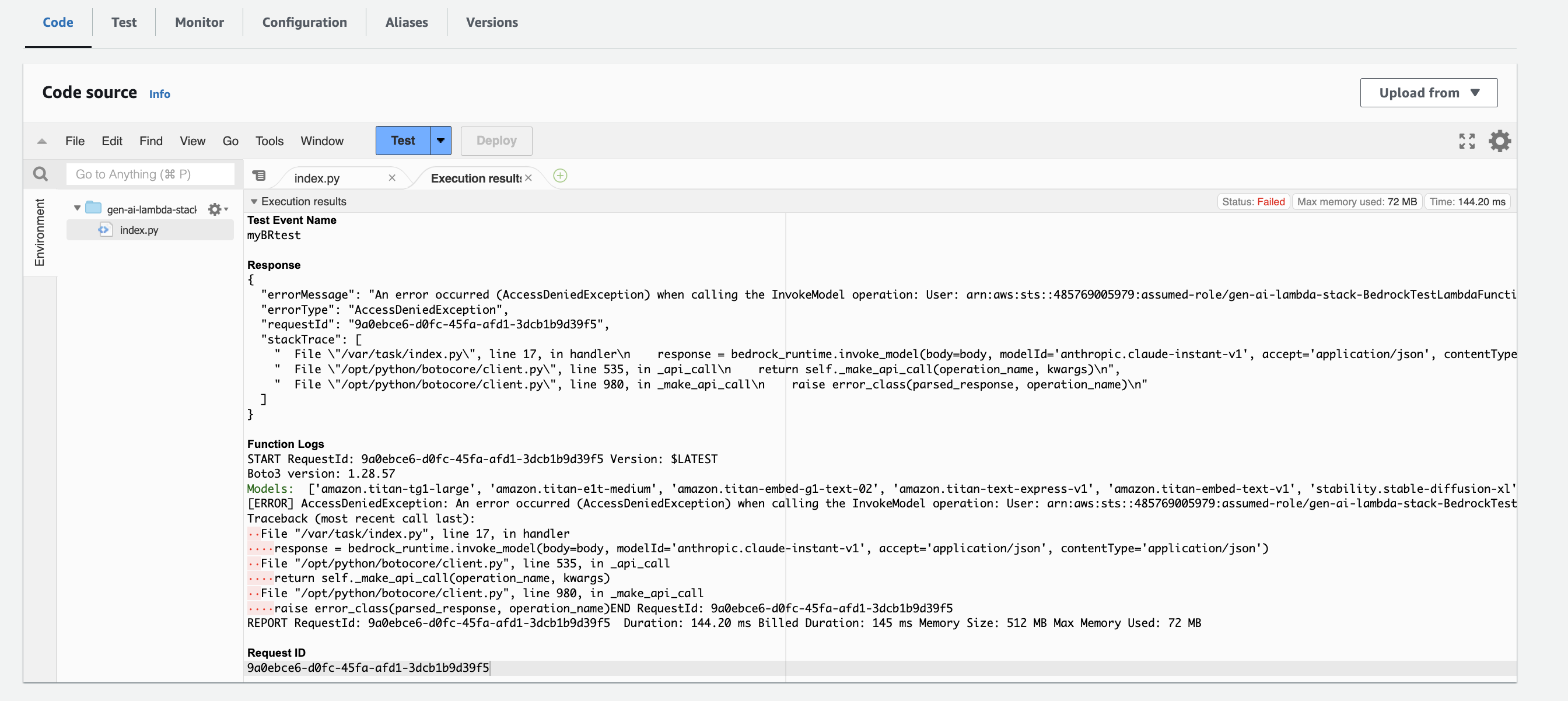
Through this testing process, we demonstrate how traffic from your VPC to the Amazon Bedrock API endpoint goes through the PrivateLink connection and not through the Internet connection.
Clean
Follow these steps to avoid incurring future charges:
- Clean up the VPC endpoints.
- Clean up the VPC.
- Delete the CloudFormation stack.
Conclusion
In this post, we demonstrate how to configure and operationalize a private connection between a generative ai workload deployed in your customer’s VPC and Amazon Bedrock using an interface VPC endpoint powered by PrivateLink. By using the architecture discussed in this post, traffic between your customer’s VPC and Amazon Bedrock will not leave Amazon’s network, ensuring that your data is not exposed to the public Internet and therefore helping you with your compliance requirements.
As a next step, test the solution in your account and share your feedback.
About the authors
 Ramirez Vittal is a Principal Architect of Machine Learning Solutions at AWS. He has over three decades of experience architecting and building distributed, hybrid, and cloud applications. He is passionate about creating secure and scalable ai/ML and big data solutions to help enterprise customers in their cloud adoption and optimization journey to improve their business results. In his free time, he rides a motorcycle and walks with his 3-year-old Sheepadoodle.
Ramirez Vittal is a Principal Architect of Machine Learning Solutions at AWS. He has over three decades of experience architecting and building distributed, hybrid, and cloud applications. He is passionate about creating secure and scalable ai/ML and big data solutions to help enterprise customers in their cloud adoption and optimization journey to improve their business results. In his free time, he rides a motorcycle and walks with his 3-year-old Sheepadoodle.
 Ray Khorsandi is an ai/ML Specialist at AWS, supporting strategic customers with ai/ML best practices. With an M.Sc. and Ph.D. In Electrical and Computer Engineering, he leads companies to create secure and scalable big data and ai/ML solutions to optimize their cloud adoption. His passions include computer vision, NLP, generative ai, and MLOps. Ray enjoys playing soccer and spending quality time with family.
Ray Khorsandi is an ai/ML Specialist at AWS, supporting strategic customers with ai/ML best practices. With an M.Sc. and Ph.D. In Electrical and Computer Engineering, he leads companies to create secure and scalable big data and ai/ML solutions to optimize their cloud adoption. His passions include computer vision, NLP, generative ai, and MLOps. Ray enjoys playing soccer and spending quality time with family.
 michael daniels is an ai/ML specialist at AWS. His expertise lies in creating and leading ai/ML and generative ai solutions for complex and challenging business problems, which is enhanced by his Ph.D. from the Univ. of Texas and his M.Sc. in Computer Science with a specialization in Machine Learning from the Georgia Institute of technology. He excels at applying cutting-edge cloud technologies to innovate, inspire and transform industry-leading organizations, while effectively communicating with stakeholders at any level or scale. In his free time, you can find Michael skiing or snowboarding in the mountains.
michael daniels is an ai/ML specialist at AWS. His expertise lies in creating and leading ai/ML and generative ai solutions for complex and challenging business problems, which is enhanced by his Ph.D. from the Univ. of Texas and his M.Sc. in Computer Science with a specialization in Machine Learning from the Georgia Institute of technology. He excels at applying cutting-edge cloud technologies to innovate, inspire and transform industry-leading organizations, while effectively communicating with stakeholders at any level or scale. In his free time, you can find Michael skiing or snowboarding in the mountains.
 NEWSLETTER
NEWSLETTER





