The routing mechanism of MoE models poses a major privacy challenge. Optimize the performance of the LLM large language model by selectively activating only a fraction of its total parameters while making it highly susceptible to adversarial data extraction through routing-dependent interactions. This risk, most obviously present with the ECR mechanism, would allow an attacker to divert user input by placing their crafted queries in the same processing batch as the target input. The MoE Tiebreak Leakage Attack exploits such architectural properties, revealing a deep privacy design flaw that therefore needs to be addressed when such MoE models are generally implemented for real-time applications that require efficiency and security in data usage.
Current MoE models employ selective token activation and routing to improve efficiency by distributing processing across multiple “experts,” thereby reducing computational demand compared to dense LLMs. However, such selective activation introduces vulnerabilities because its batch-dependent routing decisions make the models susceptible to information leakage. The main problem with routing strategies is that they treat tokens deterministically and do not guarantee independence between batches. This batch dependency allows adversaries to exploit routing logic, gain access to private entries, and expose a fundamental security flaw in models optimized for computational efficiency at the expense of privacy.
Google DeepMind researchers address these vulnerabilities with MoE Tiebreak Leakage Attack, a systematic method that manipulates MoE routing behavior to infer user cues. This attack approach inserts crafted inputs along with a warning from the victim that exploits the deterministic behavior of the model in terms of tie-breaking, where an observable change is observed in the output when the assumption is correct, causing warning tokens to be leaked. . Three fundamental components comprise this attack process: (1) token guessing, in which an attacker investigates possible warning tokens; (2) expert buffer manipulation, through which padding sequences are used to control routing behavior; and (3) routing path recovery to check the correctness of guesses from variations in output differences in multiple batch orders. This reveals a previously unexamined side-channel attack vector of MoE architectures and requires privacy-focused considerations during model optimization.
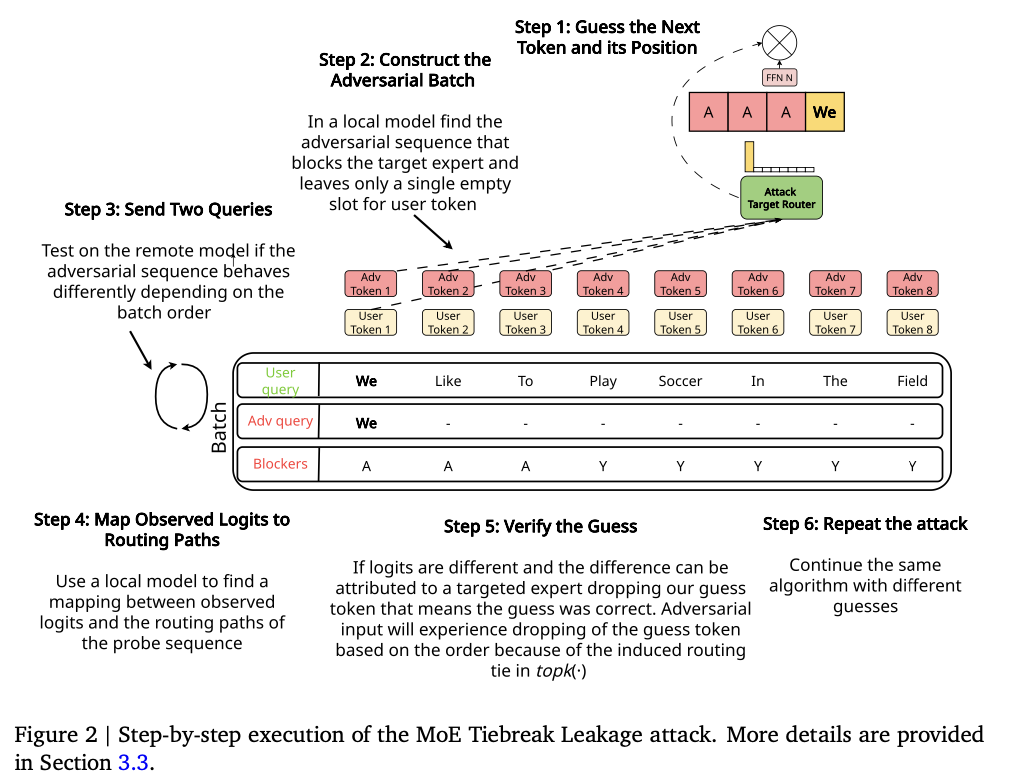
The MoE tiebreaker leakage attack is experimented on an eight-expert Mixtral model with ECR-based routing, using the PyTorch CUDA top-k implementation. The technique reduces the vocabulary set and handcrafted filler sequences in a way that affects the abilities of experts without making the traversal unpredictable. Some of the most critical technical steps are as follows:
- Token Polling and Verification: Made use of an iterative token guessing mechanism where the attacker's assumptions are aligned with the victim's message by observing differences in routing, indicating a correct assumption.
- Controlling expert capacity: The researchers used filler sequences to control the buffer capacity of the experts. This was done so that specific tokens would be sent to the intended experts.
- Path Analysis and Output Mapping: Using a local model that compares the outputs of two adversely configured batches, routing paths with token behavior mapped to each probe input were identified to verify successful extractions.
The evaluation was performed on messages of different lengths and token configurations with very high accuracy in token recovery and a scalable approach to detect privacy vulnerabilities in routing-dependent architectures.
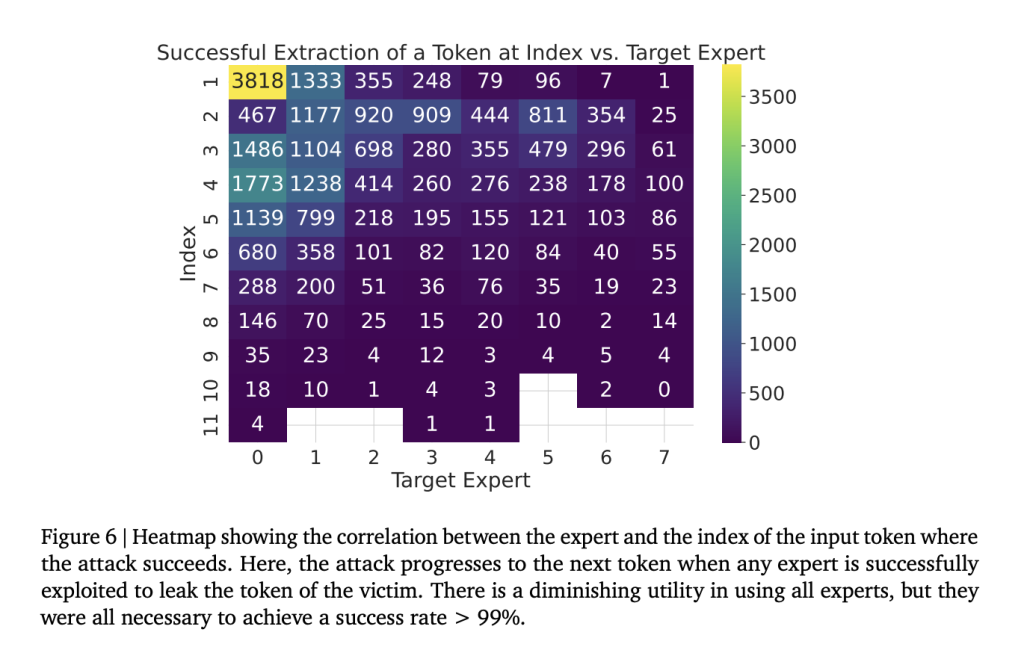
The MoE breakout leak attack was surprisingly effective: it recovered 4,833 of 4,838 tokens, with an accuracy rate of over 99.9%. Results were consistent across all configurations, with strategic padding and precise routing controls facilitating fast, near-complete extraction. By using local model queries for most interactions, the attack optimizes efficiency without relying heavily on target model queries to significantly improve the practicality of real-world applications and establish scalability of the approach for various MoE configurations and settings.
This work identifies a critical privacy vulnerability within MoE models by exploiting the potential of batch-dependent routing in ECR-based architectures to extract conflicting data. The systematic recovery of sensitive messages from users through the deterministic routing behavior enabled by the MoE tiebreak leak attack shows the need for secure design within routing protocols. Future model optimizations should take into account potential privacy risks, such as those that may be introduced by randomization or applying batch independence in routing, to reduce these vulnerabilities. This work emphasizes the importance of incorporating security assessments into architectural decisions for MoE models, especially when real-world applications increasingly rely on LLMs to handle sensitive information.
look at the Paper. All credit for this research goes to the researchers of this project. Also, don't forget to follow us on twitter.com/Marktechpost”>twitter and join our Telegram channel and LinkedIn Grabove. If you like our work, you will love our information sheet.. Don't forget to join our SubReddit over 55,000ml.
(Sponsorship opportunity with us) Promote your research/product/webinar to over 1 million monthly readers and over 500,000 community members
Aswin AK is a consulting intern at MarkTechPost. He is pursuing his dual degree from the Indian Institute of technology, Kharagpur. He is passionate about data science and machine learning, and brings a strong academic background and practical experience solving real-life interdisciplinary challenges.
<script async src="//platform.twitter.com/widgets.js” charset=”utf-8″>






