We are inundated with multiple forms of data. Whether it is data from a financial, health, educational sector or an organization. The privacy and security of that data is an important need and concern for all organizations due to the frequent attacks that occur. Attacks on computer systems can result in the loss of confidential information and can have serious consequences in terms of reputational damage, legal liability and financial loss. It can lead to unauthorized access to data.
One particular type of attack on systems that poses significant threats is the cache timing attack (CTA). Time cache attacks are security attacks that exploit the time cache behavior in computer systems. Caches are small, high-speed memory components that store frequently accessed data, reducing memory access latency and improving overall system performance. The basic idea behind cache timing attacks is for the attacker to carefully control their own memory accesses to induce specific cache behavior.
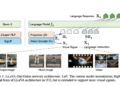
Currently, the techniques used to detect cache synchronization attacks rely heavily on heuristics and expert knowledge. This reliance on manual input can lead to fragility and an inability to adapt to new attack techniques. A solution called MACTA (Multi-Agent Cache Timing Attack) has recently been proposed to overcome this problem. MACTA uses a multi-agent reinforcement learning (MARL) approach that leverages population-based training to train both attackers and detectors. By employing MARL, MACTA aims to overcome the limitations of traditional detection techniques and improve the overall effectiveness of time-cache attack detection.
For the development and evaluation of MACTA, a realistic simulated environment called MA-AUTOCAT has been created, which allows the training and evaluation of cache-timing detectors and attackers in a controlled and reproducible way. By using MA-AUTOCAT, researchers can study and analyze the performance of MACTA under various conditions.
The results have shown that MACTA is an effective solution that does not require manual input from security experts. MACTA detectors demonstrate a high level of generalizability, achieving a 97.8% detection rate against a heuristic attack that was not exposed during training. Additionally, MACTA reduces the attack bandwidth of reinforcement learning (RL)-based attackers by an average of 20%. This reduction in attack bandwidth highlights the effectiveness of MACTA in mitigating cache timing attacks. Against an invisible SOTA detector, the average evasion rate of MACTA attackers reaches up to 99%. This indicates that MACTA attackers are highly capable of evading detection and represent a significant challenge to current detection mechanisms.
In conclusion, MACTA offers a new approach to mitigate the threat of cache synchronization attacks. By using MARL and population-based training, MACTA improves the adaptability and effectiveness of time-cache attack detection. Therefore, this looks very promising to address security vulnerabilities.
review the Research work and Code. Don’t forget to join our 20k+ ML SubReddit, discord channel, and electronic newsletter, where we share the latest AI research news, exciting AI projects, and more. If you have any questions about the article above or if we missed anything, feel free to email us at asif@marktechpost.com

Tanya Malhotra is a final year student at the University of Petroleum and Power Studies, Dehradun, studying BTech in Computer Engineering with a specialization in Artificial Intelligence and Machine Learning.
She is a data science enthusiast with good analytical and critical thinking, along with a keen interest in acquiring new skills, leading groups, and managing work in an organized manner.
 NEWSLETTER
NEWSLETTER