Anomaly detection has gained ground in various fields, such as surveillance, medical analysis, and network security. Autoencoder (AE) models, which are typically approached as a one-class classification problem, are commonly used. However, EAs tend to reconstruct anomalies too well, reducing discrimination between normal and abnormal data. Memory-based networks and pseudoanomalies have been proposed to address this, but with limitations.
The introduction of memory mechanisms in AE models aims to limit their ability to reconstruct anomalies. However, this approach may inadvertently affect normal data reconstructions. Another strategy involves generating pseudoanomalies, either by maximizing or minimizing the reconstruction loss. The above methods rely on strong inductive bias or hand-crafted augmentation techniques.
The researchers proposed a method that involves creating pseudoanomalies by incorporating adaptive noise into normal data. This is achieved by training another network to generate noise based on a normal input, which is then added to the input to create pseudoanomalies. By training an EA to poorly reconstruct these pseudoanomalies, the reconstruction boundary evolves, improving anomaly detection. Unlike methods with a strong inductive bias, this approach is generic and applicable in various domains, as demonstrated in several data sets.
Their method aims to improve anomaly detection by training an AE to reconstruct normal input well while reconstructing anomalies poorly, which is achieved by incorporating learned adaptive noise into the normal data. This noise, generated by another autoencoder, creates pseudoanomalies, which the AE reconstructs poorly. The training process ensures that the AE evolves its reconstruction boundary towards better anomaly detection. Unlike methods with a strong inductive bias, this approach is generic and applicable in various domains. During testing, anomaly scores are calculated based on the reconstruction error, providing efficient inference without additional computational cost.
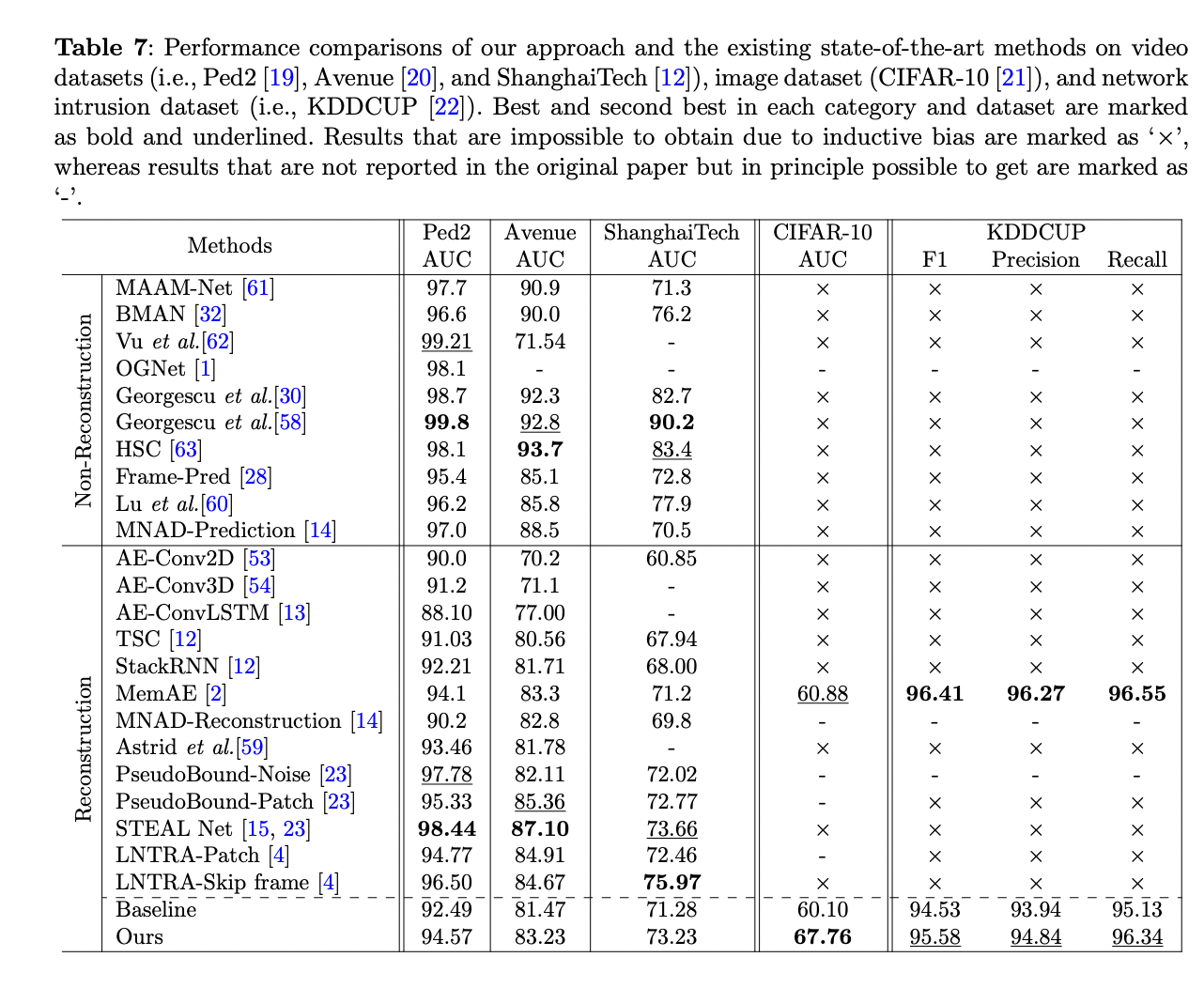
Starting with the definition of data sets and evaluation criteria. The researchers evaluated their method on various data sets, including surveillance videos (Ped2, Avenue, ShanghaiTech), CIFAR-10 images, and the KDDCUP99 network intrusion data set. They preprocess the inputs accordingly and set hyperparameters using the Adam optimizer. Their approach is widely compared with baselines and state-of-the-art methods, showing its effectiveness and generic applicability.
Summary
- The researchers introduced a robust approach to generate pseudoanomalies by incorporating noise without inductive bias.
- They used an additional autoencoder to learn the noise generation, improving the learnability.
- Performed ablation studies and evaluations on various data sets.
- Demonstrated superiority and generic applicability in video, image and network intrusion domains.
- They compared the performance of the method with existing state-of-the-art methods.
Review the Paper. All credit for this research goes to the researchers of this project. Also, don't forget to follow us on twitter.com/Marktechpost”>twitter. Join our Telegram channel, Discord channeland LinkedIn Grabove.
If you like our work, you will love our Newsletter..
Don't forget to join our 42k+ ML SubReddit
![]()
Asjad is an internal consultant at Marktechpost. He is pursuing B.tech in Mechanical Engineering at Indian Institute of technology, Kharagpur. Asjad is a machine learning and deep learning enthusiast who is always researching applications of machine learning in healthcare.
(Recommended Reading) GCX by Rightsify – Your go-to source for high-quality, ethically sourced, copyright-cleared ai music training datasets with rich metadata
<script async src="//platform.twitter.com/widgets.js” charset=”utf-8″>
 NEWSLETTER
NEWSLETTER




