According to reports, social engineering scammers are using false job offers and a new application loaded with malware called “grasscall” to install information theft software that seeks cryptographic wallets to drain.
Bleeping computer <a target="_blank" data-ct-non-breakable="null" href="https://www.bleepingcomputer.com/news/security/grasscall-malware-campaign-drains-crypto-wallets-via-fake-job-interviews/” rel=”null” target=”null” text=”null” title=”null”>reported On February 26, the actors behind the scam have now abandoned the scheme, with websites and LinkedIn accounts tied to the withdrawal scam, since the hundreds of attacked people have spoken, some who said they had their cryptographic wallets raided after downloading Grasscall.
According to reports, the Russian cyber crime group “Crazy Evil” is behind the scam, which consists in social engineering specialists, commonly known as a “team of traffickers”, which focuses on stealing cryptography.
The cybersecurity firm recorded Future reported In January, he linked “more than ten active scams on social networks” with Crazy Evil, which said “explicitly victimizes the cryptocurrency space with custom spear lures.”
One of Crazy Evil's scams, called Gatherum, seems to be an earlier iteration of Grasscall, since it has disguised a similar meeting application with the same logo and brand.
Cointelegraph found an x <a target="_blank" data-ct-non-breakable="null" href="https://x.com/VibeCallapp” rel=”null” target=”null” text=”null” title=”null”>account Called “Vibecall” with the same logo and marks as Gatherum and Grasscall. It seems that the account was active in mid -February despite its June 2022 creation date.
A comparison from side to side accounts of Gatherum and Vibecall. Source: x
According to the reports, the last scheme of Crazy Evil involved a false cryptography firm called “Surker de Cadena”, which had several social media accounts that created work listings on LinkedIn and in the popular web job search sites Cryptojobslist and well.
Those who requested the works were sent an email from the firm asking them to communicate with their marketing boss in Telegram, who would then ask the objective to download the Malicious Grasscall application of a website under the control of the group, which has now been scrubbed.
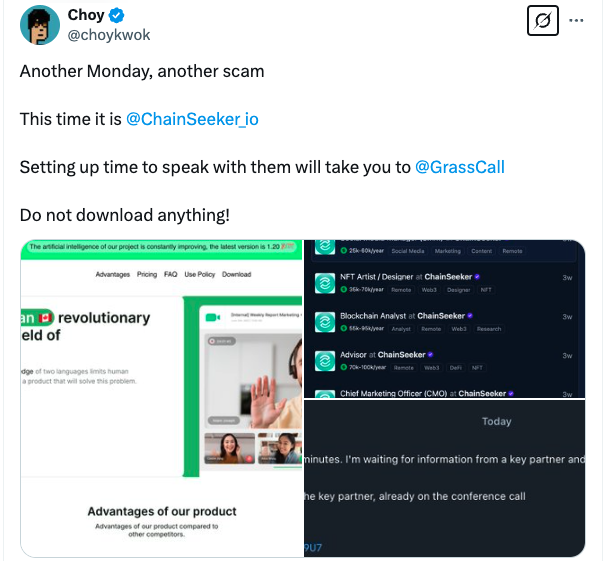
Fountain: <a target="_blank" data-ct-non-breakable="null" href="https://x.com/choykwok/status/1893972018405527594″ rel=”null” target=”null” text=”null” title=”https://x.com/choykwok/status/1893972018405527594″>Choy
Dozens of x and LinkedIn publications of employment search engines seen by Cointelegraph reported a request for a role in Chain Seeker just to receive the malicious link.
“This scam was extremely well orchestrated: they had a website, LinkedIn and x profiles and listed employees,” LinkedIn User Cristian Ghita listed aware to the platform on February 26 after requesting a role with the company.
“It seemed legitimate from almost all angles. Even the videoconference tool had an almost credible online presence, ”Ghita added.
Related: Computer pirates are doing github false projects to steal cryptography: Kaspersky
The work ads published by Chain Seeker had been mainly removed by several Job Board sites, except one still active in LinkedIn at the time of writing.
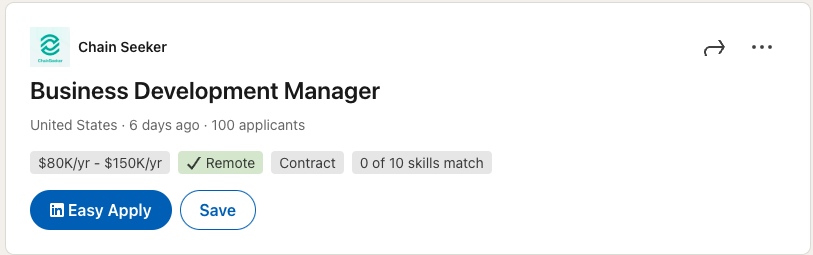
An offer of work by Chain Seeker promises up to $ 150,000 a year salary for a business development manager. Source: LinkedIn
A website for the chain search engine lists a financial director named Isabel Olmedo and a human resources manager called Adriano Cattaneo, both whose LinkedIn pages had been cleaned. A account Under the name of Arjoms, Dzalbs was still active and was observed as the firm's CEO.
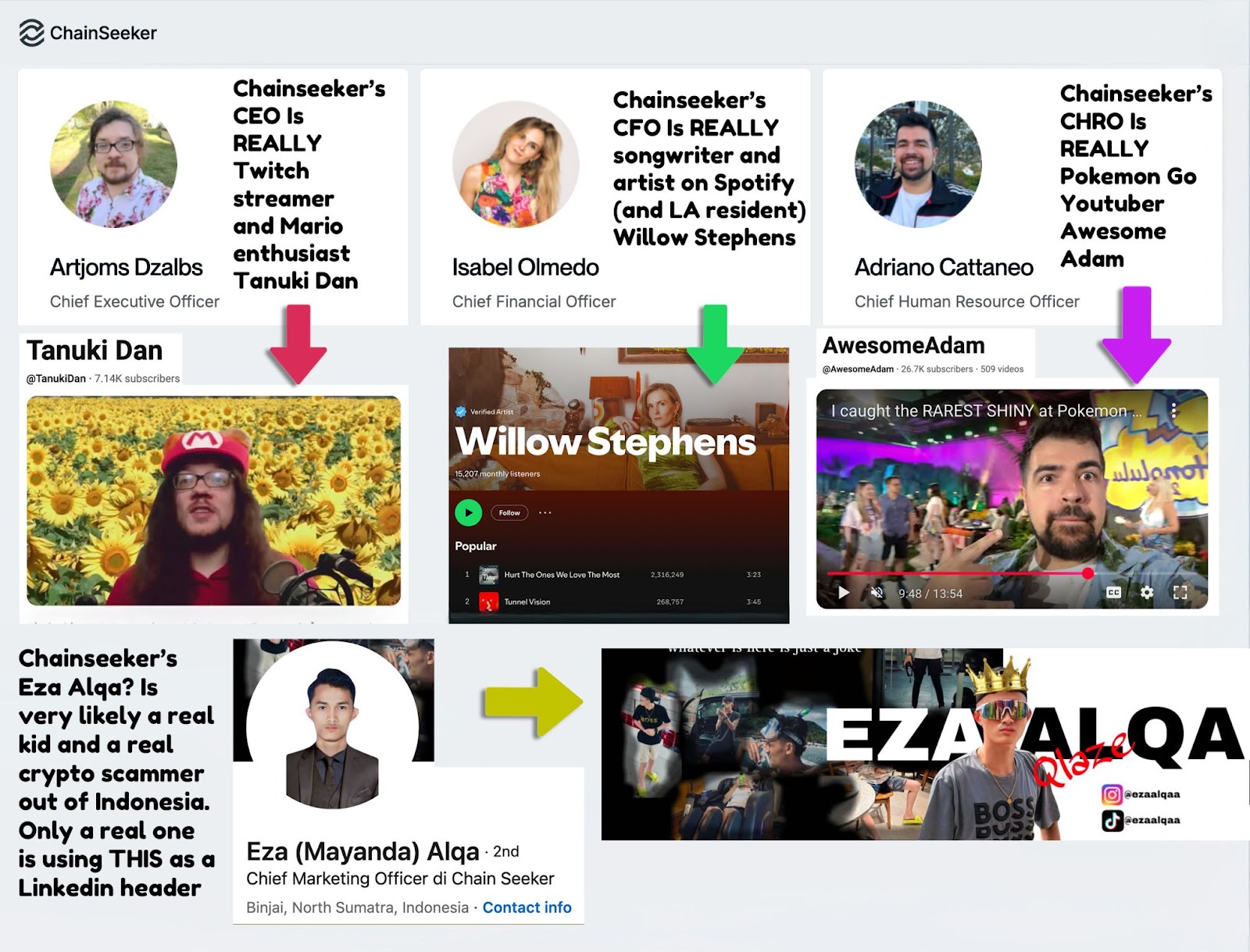
LinkedIn user, Riley Robbins, discovered that the alleged executive team of the search engine used the similarity of several online personalities. Fountain: Riley Robbins/LinkedIn
In his report last month, the registered future warned the merchants of crypto and Token non -fungible (nft) and play professionals “are main objectives.”
Many users in x and LinkedIn advised those who believe they are affected by Grasscall malware that use a device not infected to change passwords and move their crypt to fresh wallets as caution.
Magazine: False Rabby Wallet Scam linked to Dubai crypto CEO and many more victims
 NEWSLETTER
NEWSLETTER





