Blockchain bridges allow decentralized finance (DeFi) users to use the same tokens across multiple blockchains. For example, a merchant can use USD Coin (USDC) on the Ethereum or Solana blockchains to interact with decentralized applications (DApps) on those networks.
While these protocols may be convenient for DeFi users, they are at risk of being exploited by malicious actors. For example, last year the Wormhole Bridge, a popular cross-chain crypto bridge between Solana, Ethereum, Avalanche, and others, was hacked, with attackers stealing more than $321 million worth of wrapped Ethereum (wETH), the largest ever hack ever. in DeFi history of the time.
Just over a month later, on March 23, 2022, the Ronin Network bridge, Axie Infinity’s Ethereum-based sidechain, was hacked for over $620 million, and on August 2, the Nomad bridge was hacked by over $190 million. In total, more than $2.5 billion was stolen from chain-link bridges between 2020 and 2022.
Trustless bridging, known as non-custodial or decentralized bridging, could improve the security of users in cross-chain transfers.
What is a blockchain bridge?
A cross-chain bridge is a technology that allows assets or data to be sent from one blockchain network to another. These bridges allow two or more separate blockchain networks to communicate with each other and share information. The interoperability provided by cross-chain bridging makes it possible to move assets from one network to another.
Recent: SEC vs. Kraken: A Single or Opening Salvo in an Assault on Crypto?
Most bridging technologies use smart contracts on both blockchains to make cross-chain transactions possible.
Cross-chain bridges can move many assets, such as cryptocurrencies, digital tokens, and other data. Using these bridges makes it easier for different blockchain networks to work together and for users to take advantage of the unique features and benefits of each network.
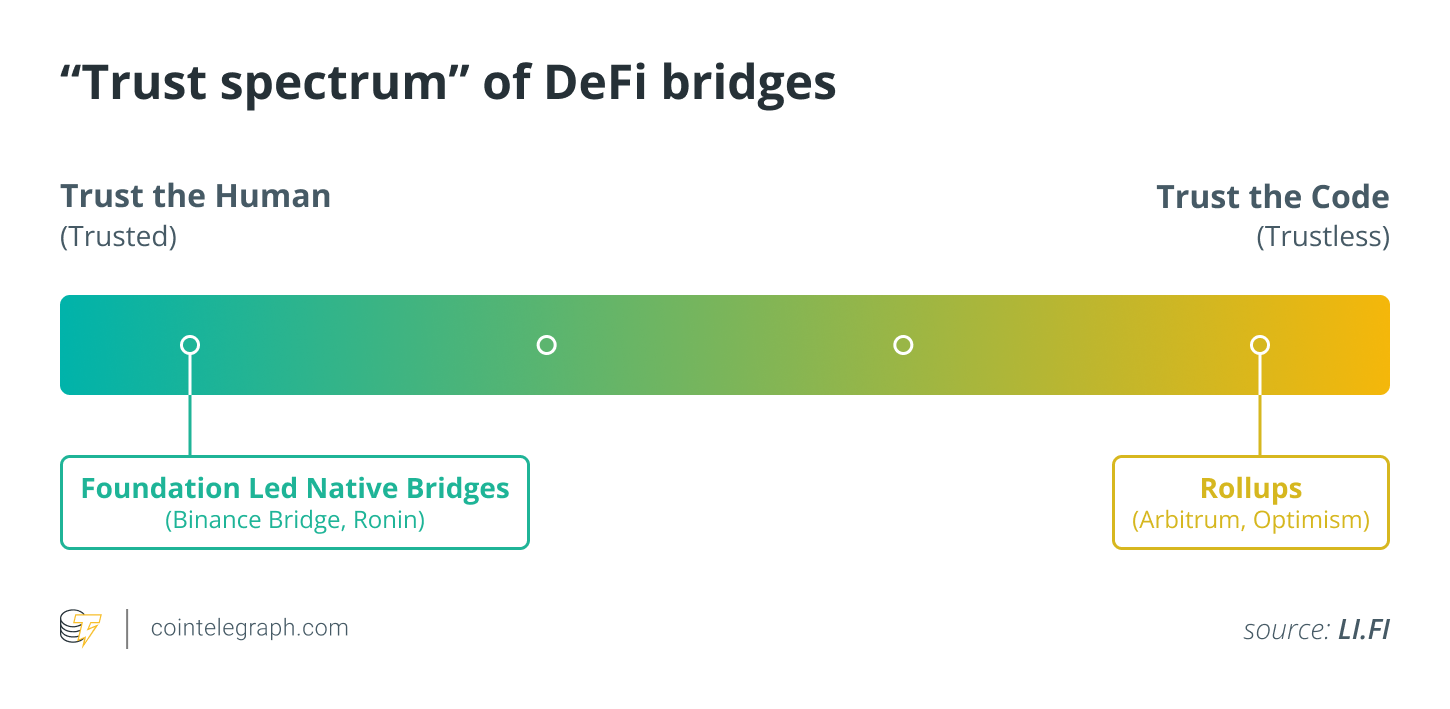
Trusted vs. Trustless Bridges
When it comes to bridging protocols, there are two main types, centralized (trusted) bridging and decentralized (untrusted) bridging. Trusted bridges are managed by centralized entities that take custody of the tokens once they are transferred to the bridge. A major risk with escrow bridges is the single point of failure (the centralized escrow), making it an easier target for hacking attempts.
Instead of using centralized custodians to transfer tokens through blockchains, trustless bridges use smart contracts to complete the process.
Smart contracts are automated programs that perform certain actions once conditions are met. Because of this, trustless bridges are seen as a more secure alternative as each user retains custody of their tokens during the transfer process.
However, trustless bridges can still be compromised if the smart contract code has vulnerabilities that are not identified and patched by the development team.
Pascal Berrang, a blockchain researcher and core developer of Nimiq, a blockchain-based payment protocol, told Cointelegraph: “In general, the use of interchain bridging presents additional risks over using a single blockchain. “.
“It increases the attack surface through blockchains, potential custodians, and smart contracts. There are various types of chain bridges, which come with different tradeoffs in terms of these risks.” He continued:
“Cross-chain bridges naturally involve two or more blockchains, often using different security mechanisms. Therefore, the security of the bridged assets depends on the weakest blockchain involved in the bridge. For example, if one of the blockchains is attacked, it would be possible to reverse an interchain trade on one of the chains but not the other, resulting in an imbalance of assets.”
Berrang also highlighted vulnerabilities related to bridged assets that are locked in the bridge. “Funds are typically stored or locked in a central location, constituting a single point of failure. Depending on the type of bridge, these funds are subject to different risks: In a smart contract-based bridge, errors in those contracts can render the bridge assets worthless,” Berrang said.
“An example could be a bug that allows infinite minting of new bridged tokens. Bridges operated by trusted custodians are subject to counterparty risk if the custodians misbehave or have their keys stolen,” she added.
Jeremy Musighi, head of growth at Balancer, an automated market maker, believes that additional risks lie in the complexity of blockchain bridging, telling Cointelegraph that “cross-chain bridging carries several significant risks. Security is one of the biggest risks; Due to the complexity and difficulty of implementing cross-chain bridging, they are prone to bugs and vulnerabilities that malicious actors can exploit to steal assets or perform other malicious actions.”
Musighi also noted that scalability issues pose additional risks to the bridging process, stating: “Another risk is scalability, as cross-chain bridges may not be able to handle large amounts of traffic, leading to delays and higher costs.” For the users”.
Protection of bridges against exploits
Developers can prevent cross-chain bridges from being hacked by implementing various security measures that help ensure the confidentiality, integrity, and authenticity of transferred assets.
One of the most important measures is to ensure that the smart contract code that forms the core of cross-chain bridging is secure and free of vulnerabilities. This can be accomplished through regular security audits, bug bounty programs, and code reviews, which help identify and fix potential security issues.
Another measure that developers can take is to use cryptographic algorithms, such as digital signatures and hash functions, to secure the transfer of assets and information between different blockchain networks. This helps ensure that transferred assets are protected and that any malicious actors cannot interfere with the transfer process.
Additionally, regular network monitoring is essential to detect suspicious activity and prevent attacks. By monitoring the network, developers can detect any security issues and take the appropriate steps to resolve them before they do any harm.
Finally, developing and implementing secure cross-chain bridging requires following best practices, such as safe coding practices, testing and debugging, and safe deployment methods. By doing so, developers can help ensure the security and stability of cross-chain bridges.
Preventing cross-chain bridges from being hacked requires a combination of secure code, cryptographic algorithms, strong consensus mechanisms, network monitoring, and following best practices.
Are trustless bridges a better solution?
Trustless bridges can provide a more secure solution for bridging assets between blockchains only if the smart contract code has been fully audited to ensure no vulnerabilities are present.
The main security benefit of trustless bridging is that users retain custody of their tokens throughout the process, with smart contracts taking care of the transfer process. Also, the lack of a central authority to lock the tokens makes the bridges more difficult to attack, since there is no single point of failure.
Recent: Binance Banking Troubles Highlight a Divide Between Crypto Businesses and Banks
Musighi told Cointelegraph: “I generally find trustless bridges more secure than trusted bridges, as they operate transparently and rely on a decentralized network to validate and facilitate cross-chain asset transfers, whereas Trusted bridges rely on a centralized third party, which means there is a single point of failure and a concentrated attack surface for hackers to target.”
“Trustless bridges are easier to audit and come with the clear benefit of trust minimization. Since many centralized bridges also leverage (simpler) smart contracts, trustless bridges can be considered a less risky but not risk-free option,” Berrang said.
As the decentralized finance space matures, developers must take additional steps to secure cross-chain bridges. However, as cryptocurrency users become more interested in self-custody and decentralization, trustless bridges may grow in popularity.
 NEWSLETTER
NEWSLETTER





