Introduction
The evolution of humans from coal mining to data mining makes immense contributions to human growth and technological development. By changing the magnitude of the physical work involved, the weight has now shifted to the mental effort to perform this new type of mining. The data mining process includes multiple aspects, including the association rule, which is important for its practical contribution to understanding customers and driving business growth. Do you have the exact requirements? Are you interested in improving your knowledge to achieve an exponential increase in customer satisfaction? Is your goal to develop a better recommendation system that is competitive enough with big brands? Below is a brief introduction to the key concepts and fundamentals of association rules in data mining.
Learning objectives
- Understand the essence of association rules as if/then statements that reveal relationships within data.
- Identify and differentiate applications such as shopping basket analysis, fraud detection, and recommendation systems, showing the versatility and practical importance of association rules.
- Learn how association rules work, exploring the role of cardinality, support, confidence, and elevation in predicting and evaluating relationships within data sets.
What are association rules in data mining?
Defined by their names, association rules are if/then statements that identify relationships or dependencies between data. With the characteristic property of adapting to numerical and non-numeric categorical data, it is often applied in shopping basket analysis and other applications. It can absorb data from relational and transactional databases and other data sources.
The association rule has two parts: antecedent or if and consequent or then. The antecedent is the first part available in the data, while the resultant is the resulting part available in combination with the antecedent. For example, the shopping basket analysis example would be: “If a customer buys running shoes, there is a chance that he will also buy energy bars.” here, running shoes are an antecedent and energy bars are a consequence. The example is aimed more specifically at the fitness enthusiast public.
What are the use cases for association rules?
There are a wide variety of applications for association rules. The three main examples of association rule mining are:
Shopping Basket Analysis: An example of a purchase combination may be the purchase of yogurt, and granola is likely to be associated with the purchase of berries. Indicates the importance of the association rule in the analysis of purchasing habits and requirements. The practical use of interpretation is seen in developing appropriate bundled offerings, optimizing product placement, and increasing sales.
Fraud detection: Here, the combination of use is to identify a purchasing pattern, its location and frequency. Its recognition helps detect fraudulent activities and take preventive measures from the same IP address.
Recommendation systems: These include detecting usage patterns from browsing history and previous purchases to predict future user requirements. The recommendations are based on the same. Expanding the use of marketing is also important in music and entertainment-based services.
Source: data aspirant
How do association rules work?
The prediction in the association rule explained above with examples is calculated based on cardinality, support and confidence. Cardinality refers to the relationship between two elements, which increases proportionally with the number of objects. Support indicates the frequency of statements, and then trust informs the frequency of truthfulness of these relationships. Explain how association rules work, determining the rules that govern the reason and situation where the combination can occur. For example, the preferred healthy and less time-consuming breakfast option combines yogurt with granola and berries.
Often in practical situations the figures become unrealistic. Some statistically independent items with the lowest purchase mix could have a significantly high percentage in practical use. For example, statistically there are fewer chances of buying beer and diapers combined, while real-world statistics are comparatively higher. Increasing stats is a boost.
Measures of the effectiveness of association rules
The effectiveness of association rules is mainly measured by support, trust, and momentum. Support refers to the frequency and high support indicates the commonality of the quantity in the data set. Confidence measures the reliability of the association rule. High confidence suggests that A and B are proportional and therefore increase in direct relation to each other.
Lift compares the item dependency. If the statistical and practical numbers are equal or the antecedent and consequent are equal, the elevation will be 1 and the associated objects are independent. Objects depend on each other if elevation > 1 and the antecedent is greater than the consequent. Furthermore, the combination negatively impacts each other if the consequent is greater than the antecedent with elevation <1.
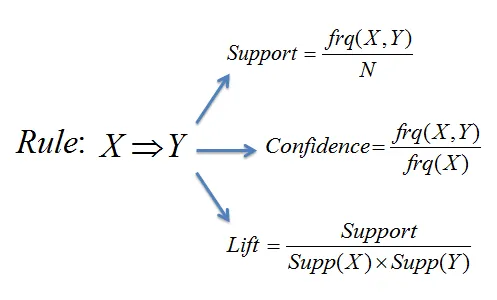
Source: Data Mining Map
Association Rules Algorithms
Three algorithms generate association rules. These are expressed as follows:
A priori algorithm
The association rules in the a priori algorithm are generated through frequent transaction data sets. It is often used for basket analysis and uses techniques such as breadth-first search and Hash Tree. By providing information on combination products purchased together, it also serves medical purposes by finding drug reactions in patients.
Éclat Algorithm
Also known as equivalent class transformation, it uses a depth-first search technique. Providing fast and accurate execution, it also addresses transactional databases. The ELCAT algorithm uses less storage and works without repeated scans of data to calculate individual support values. Instead, it uses transaction ID sets or Tidsets for calculation purposes.
FP growth algorithm
Known as Frequent Pattern Growth, it is an improved version of the Apriori algorithm. It is analyzed through two steps. The first is the conversion of the database into a tree structure, thus earning the name due to the representation of frequent patterns. The second step is the representation format, which makes it even easier to extract the most frequent patterns.

Source: Research Gate
Conclusion
Data mining refers to the extraction of information from entire data sets. Association rule mining is the method of identifying correlations, patterns, associations or causal structures in data sets. With the immense scope of applicability in retail, healthcare, fraud detection, biological research and many other fields, the association rule works through the if/then statement. Support, trust, and drive play critical roles in evaluating your effectiveness. Furthermore, the development of association rules occurs using three algorithms. Get introduced in detail to most important concepts along with learning association rules in data mining with our data science course.
Key takeaways
- Association rules find practical use in various fields, such as optimizing product placement in shopping basket analysis, flagging fraudulent activities in fraud detection, and improving user experience through recommendation systems.
- Support, trust, and momentum are crucial metrics for evaluating the effectiveness of association rules, providing information on the frequency, reliability, and dependence of the identified relationships.
- Explore three key algorithms (Apriori, Eclat, and FP Growth) that drive association rule generation, each offering unique advantages in terms of execution speed, data scanning efficiency, and application scope.
Frequent questions
A. The drawbacks are many rules, long procedures, poor performance, and the inclusion of many parameters in association rule mining.
A. Yes, there are four types of association rules in mining. These are multirelational, quantitative, generalized and interval information association rules.
A. The important tools in the association rule are RapidMiner, WEKA and Orange.






